There is so many ways to hack a WordPress Website, pirates already know it better than anyone else. But do you know it too? Do you know against what you need to be protected?
It’s important to learn how a website can be broken, stolen, how intruders can take your place.
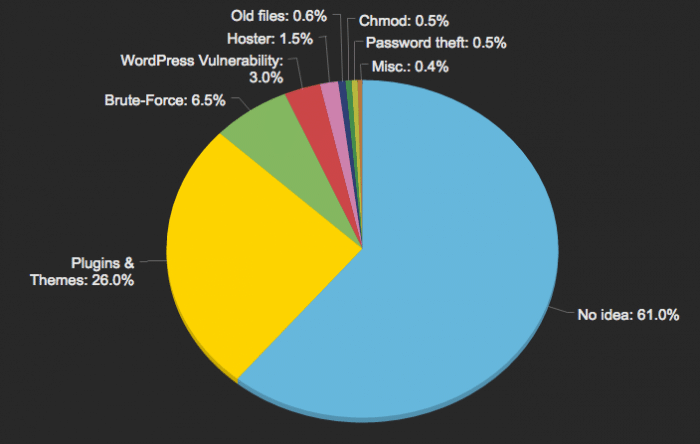
Here’s some stats from our clients since 2010:
- 60% of hacked people don’t even know what happened,
- 25% of pirates exploited a vulnerability in a plugin or theme,
- 6,5% came with your password, found by brute-force,
- 3% used a flaw from the WordPress core not updated,
- 1,5% get hacked because of their host provider,
- 0,6% of websites still had old installation files,
- 0,5% because of bad files permissions (chmod),
- 0,5 because of a stolen password (without brute-force)
- 0,4% sharing other reasons like computer without antivirus, answer to a phishing mail, outdated server softwares or FTP software, etc
Don’t Know What Happened
This is badly common, but for more than a half of WordPress hacked websites – 61% –, the source of the issue is not clear. It’s even difficult to know how it happened, where is the entry point, where are the hints, who and why they did that. Webmasters were just victims of hackers, hacking websites.
In those cases, the work to try to know the reasons of the hack is too big and too expensive for a client to work on.
And if it happens to you a day, I recommend you to don’t waste your time, what happened is really bad, but use this time to secure your website instead of doing this useless investigation.
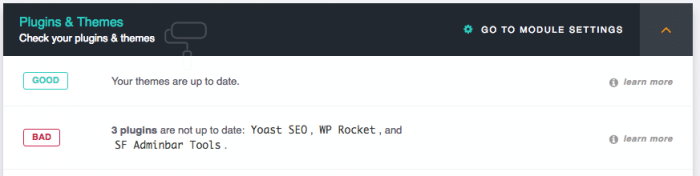
A Plugin or Theme is Vulnerable
Without plugins or theme, WordPress wouldn’t be what it is today. We all need these additional components so every website can respond to a need. The number of plugins is growing everyday, everybody can be an author, regardless of their development skill.
Keep Up to Date
The first thing to know with plugins and theme is to be up to date. We always say that but it’s very important, don’t forget the goal of the updates, correcting bugs, adding new features but also patching security vulnerabilities!
Trust
Don’t rely on plugins which weren’t updated since 2 years at least, neither the ones without a good support, or too few downloads when the author isn’t known yet.
This trust has to be earned, it is possible that this plugin with 10 downloads done by a new author is perfect, but wait that the trust has been brought by the community.
Downloads
For the free ones, prefer plugins from the official WordPress Repository because it’s examined a minimum by Mika and Otto whom doing a great job on that (see “How to Review a Plugin” on wordpress.tv).
If it’s a premium one – so it’s not in the repo – don’t try to find it using search engines because they will find it on warez websites. This is the best way to get a WordPress Hacked Website.
What you’ve earned with this fake free product is null besides what you’ll have to do, and pay to get your website back on its legs again.
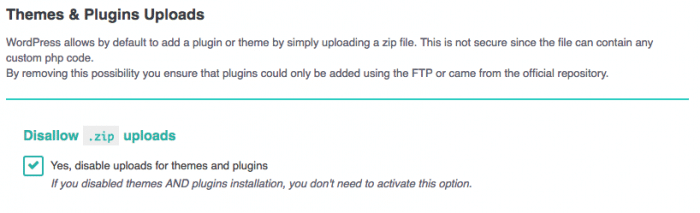
Uploads
With WordPress it’s possible to send plugins using the admin area, with a simple .zip file, and it’s done! But, this file can contain any code and will still be installed. Here’s the best way to get a WordPress Website Hacked.
The best way to be secure is, again, to only use plugins from the repository and for premium ones to use a secure FTP.
Brute-Force on Passwords
Brute-force is a way to rob passwords, mainly the short or weak ones like azerty or your_birthday like.
Usernames
Don’t use common usernames like admin or administrator or even your usual name/nickname. To launch a brute-force more easily, the good thing is to know the login, if yours is complex like i_was_born_admin_in_1979%%% it’s more difficult to get in, also create an email address dedicated to this admin account.
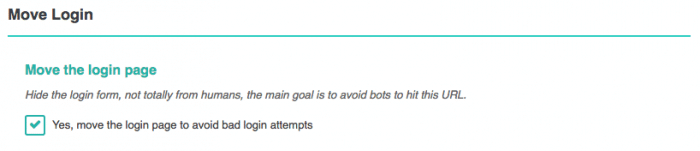
Move the Login Page
By moving the login page, bots can’t even try to log in, blocked since the first try they will stop by themselves, without any risks for you.
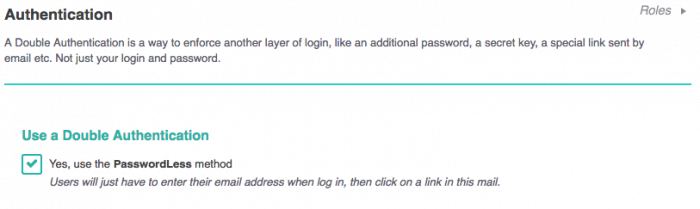
Double Authentication
The best result is done with a Double Authentication because even with the password, the attacker will still need a second layer of authentication, making your website impossible to hack.
WordPress Flaw
Sometimes, it happens, WordPress contains a vulnerability. The big advantage is that we heard it when it’s already fixed, making WordPress the most secure CMS for us.
Now, it’s up to you to stay up to date, once again. Without this update, you’ll take a huge risk because the flaw is now disclosed, shared, known from everyone, pirates can now hack WordPress Websites.
Host Providers Fault
It happens that the hack is not your fault but your host provider one’s. The attacker used another way to sneak into your website : your host provider. You have to choose a good host provider known for his quality and security, i personally recommend you SiteGround.
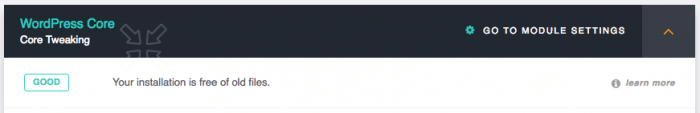
Old Files in WordPress
Did you know that since WordPress 2.0 some files were deleted from the core? If your website is up to date using the automatic installer, perfect. If, like me, you’re doing it using SFTP or GIT, you’re just copying files without any deletion, keeping the old files.
The issue is that those useless files can contains security flaws, this is why it’s important to delete them.
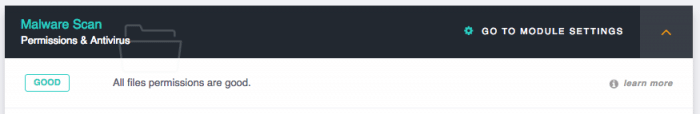
Bad Files Permissions
File and folders have permissions, reading, writing, execution, one or two or both. I’m talking here about chmod, the UNIX command you may heard about to change the perms on files.
It’s dangerous to use the 0777 value because it allows everything, read, write, execute at the same time. Correct values would be 0644 for files and 0755 for folders.
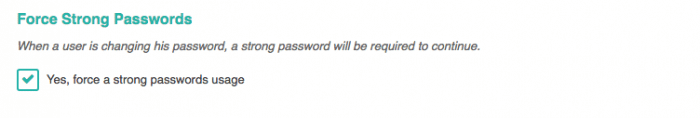
Stolen Passwords
Here, it’s your turn, you have to use a strong password. We already talked about that, i invite you to read again our post on strong passwords.
Also, if you got members, it could be great to be sure they’re using strong passwords.
Tips
Quick list of security tips because you also have to care about not visible things like:
- Use an antivirus on your computer,
- Don’t use unknown networks specially in train stations or restaurants,
- Don’t share your admin account,
- Don’t answer to email asking for personal information,
- Use a secure FTP or SSH instead of a simple FTP,
- Disconnect from your admin account when job’s done.
What about you, did you already live the hack of a WordPress Website?