Update your website now!
Yes, this is the first and last thing I have to tell you, stay updated, above all if you’re using WordPress 4.7 or 4.7.1. Older versions are not affected, even if they are using the old “REST API” plugin.
This post could only be a tweet, but I wanted to give you more informations.
About WordPress
On January 26th, WordPress 4.7.2 was released as a security update, the release notes only mentioned 3 fixes about vulnerabilities but a week later, the security team disclosed another vulnerability, much more critical than the 3 others, and it was also patched in this version 4.7.2.
Why not discloses the 4 flaws in the same time? Aaron Campbell said “We believe transparency is in the public’s best interest […] It is our stance that security issues should always be disclosed. In this case, we intentionally delayed disclosing this issue by one week to ensure the safety of millions of additional WordPress sites.”
And he’s right, I just agree with that, the usual “the sooner the better” is not welcome here.
About The Vulnerability
It’s located in the REST API core. It leads to 2 new vulnerabilities: Remote privilege escalation and Content injection bugs.
It allows unauthenticated attackers to modify the contents of any post on your WordPress website.
Technically, if you are sending a HTTP request to /wp-json/wp/v2/posts/1234, the ID parameter would be set to 1234. A bug exists because it prioritizes $_GET and $_POST values instead of the ones from the original route.
This lets attackers to send a request like: /wp-json/wp/v2/posts/1234?id=5678foobar, this will assign the value 5678foobar to the ID.
Then, it’s possible for an attacker to modify the content of any of your posted on your website. This kind of vulnerability is caused by the type-juggling issue, as shown before.
About the Hacks
Today, 6 February, there are already many many websites that are the target of this vulnerability, I mean, they are defaced! This is the last thing you need, have to manage a website deface when you wake up.
The next step of hacking using this flaw is SEO Spam, your website won’t be defaced, but you’ll have some injected content leading to a bad SEO for you, and a good one for the attackers.
About You
If you can’t update, deactivate the REST API now, you can do it just by checking a box in SecuPress.
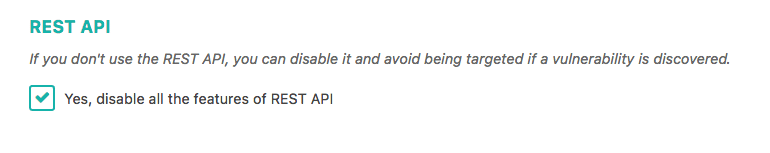
Disable all the features of REST API
If you’re using a plugin or script to disable the automatic minor updates, please remove it and let WordPress do its job to protect you.
If you are not sure if your automatic updates are available, you can just force them using SecuPress.
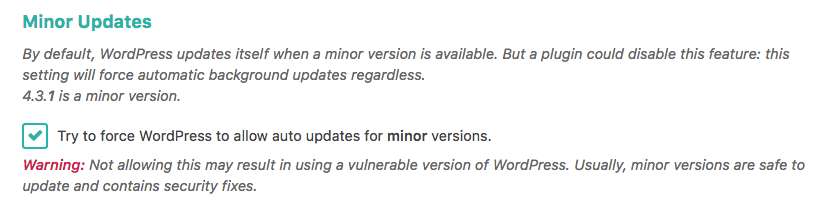
Force WordPress to allow auto updates for minor versions
Update your website now!


