WordFence was recently examined by hackers and security consultants. This allowed WordFence to improve its product in the discovery of critical security flaws.
Version 5.2.5 and recently 5.2.6 corrects these faults. Is it over? I do not think … from now read the changelog for version 5.2.5 of WordFence.
Hacker ? Consultant ?
The difference between the two is to say, in my opinion, “Black Hat” or “White Hat” or “Grey Hat”. As with SEO, Blacks Hats are the people who are not there to enforce the rules or the work of others.
When a hacker discovers flaws, several solution are then available to him:
- He said nothing to anyone, and tries to exploit the most and the longest time possible these flaws in order to use it for him (steal data to resell, get HD storage of viruses, etc.) ,
- He said nothing to the author of the plugin but spread informations on reddit or on his blog or in undergrounds boards of hackers, where they also then attempt to exploit vulnerabilities on a larger scale. In this case, the fact that many people are aware, there is a good chance that Grey Hat either the party or simply a user falling on this information decides to alert the author himself. Thanks to him.
- He points out the flaws to the author and at the same time spread on his blog and websites security flaws in 0-day mode, better but not great.
- He points out the flaws to the author, the 2 agree on a reasonable time to patch, then second wait time that users have time to keep up to date, and thereafter, he informed from his blog and site security vulnerabilities that have been patched so.
The last is the focus of SecuPress, it is also called “Responsible Disclosure” or “Responsible Disclosure” is in my opinion the least dangerous method for users. I say “less” because the flaws are exploitable sites are not taking update.
Would it not be better to say nothing and let this go quietly?
Impossible! The plugin has been updated, people (like me) will look at the changelog or differential changes in order to understand why this plugin have been updated.
Some aware people will spread these informations. Also, why would hide improvements on your products? A shame to have made a mistake? A fault confessed, half redressed no!? Say what you have improved, it can only be good for you.
The plugin RevSlider that caused numerous attacks and pirated websites because of the silence, the flaw was patched in February 2014, result: in August 2014 waves unfurled …
I come back a little on the case 1 where the hacker told anyone. The MailPoet plugin also caused some other attacks, but flaws have been discovered in July 2014 Outside, I found traces of these hacks at a client from November 2013 So there was definitely well at least one person who found these flaws and has kept silent.
What attacks?
5.2.5 fixes mainly four critical flaws discovered by SecuPress, here they are now in detail, these flaws being patched for several weeks (on 09/20/2014) I can now disclose them, with the agreement of the author of the plugin, ther very friendly Mark Maunde.
XSS
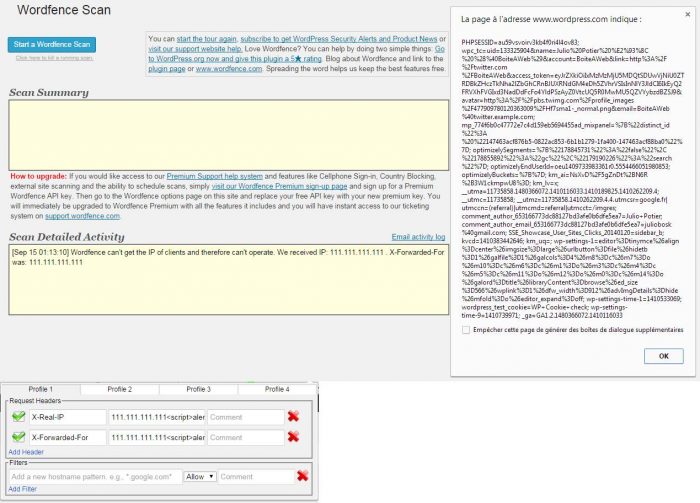
The IP address is not properly parsed:
We can then change the headers of HTTP requests using a fake IP address like this:
999.999.999.999<script>alert(/SecuPress/);</script>
HTML and JS code will be displayed as plain in the back office because the IP is not correct WordFence displays it as an alert.
Attack ByPass
Once again, changing its IP, simply put a local IP to be ignored WordFence, thinking that you are doing local tests.
127.0.0.1
With this IP, I can now bruteforce a login page of a site, I would not be blocked or logged.
Block Country ByPass
Again, the IP can be simply modified to impersonate another country, if you belong to a country forbidden to visit, changing its IP with an authorized country enough to bluff the plugin.
Anti DDoS ByPass
The plugin description says that the cache files used during a DDoS attack is used to save the site of the attack.
This is not entirely wrong, it is better to, X times, load the same cached page rather than using SQL and PHP every time.
As a reminder, a DDoS attack is aimed at bringing down the server and its services (apache, php, sql), eat it all its resources to block it.
The hacker then launches 5000 requests per second on your site until all the resources are down, and if you do not have a cache, ooch, if you have one, as the cache plugin WP Rocket, so it will to pass the course, but nothing that will not be enough, I’m afraid.
So in the code plugin we just read:
if($_SERVER['REQUEST_METHOD'] != 'GET'){ return false; } //Only cache GET's
That means I can do DDoS attacks via the HTTP POST method, I won’t go in the cache, so the cache argument against DDoS falls overboard.
if(isset($_SERVER['QUERY_STRING']) && strlen($_SERVER['QUERY_STRING']) > 0 && (! preg_match('/^d+=d+$/', $_SERVER['QUERY_STRING'])) ){ //Don't cache query strings unless they are /?123132423=123123234 DDoS style.
Also this code and its comments show that requests for HTTP GET method with a parameter will not be in the cache, which is normal, all the caching plugins do that.
That means that adding a simple parameter in my URLs for DDoS spend carefree off WordFence cache, whether the cache or FalconCache normal (= GZIP)
Closing Remarks
You should know that it is simple to change the headers queries, free browser addons exists, their use is simple.
I can only advise you to keep up to date, I can not tell you that everything is patched, just that several patches have been done.