W3 Total Cache aka W3TC is a famous caching plugin, created on 2009 by Frederick Townes. W3TC is known by everyone in the WordPress community and it’s a recommended plugin, it’s always in the top 5 caching plugins, always in good posts about performance, and even in books.

W3TC and Durability
Few months ago, on Marth 2016, Frederick has to post an explanation on WPTavern saying that his plugin was not abandoned, I personally think that if you need to post this, your plugin is already abandoned. At the moment of this post, the code of the plugin has not been updated since one year, and the support has not been done by the author itself. Only users helping each others, which is cool.
W3TC and Web Security
Like every plugin, an author can encounter some security issues, usually reported respecting a non disclose clause from the security consultant or team. As you browse all the changelogs, you can see how many security issues has been fixed during the last years, which is also cool.
But today W3TC is vulnerable to a XSS flaw, high risk rated. So, what’s next? Who will fix the issue in the repository? You may know (or not) that this plugin exists on github and has been patched, but nobody can update the one from the repository.
It means that almost everyone won’t update it and will keep the XSS risk in their administration area, which is really really bad.
When someone kindly points out a flaw in your work, don’t act offended. Simply fix it. Job done, everybody happy.
— Kitty Giraudel (@KittyGiraudel) September 22, 2016
W3TC and Adoption
WordPress plugins can be adopted, an author can add the keyword adopt-me and then give the plugin to anyone. But in our case the author doesn’t seems to respond and/or won’t give it’s plugin since, a premium version exists, still with no support, no public communication …
So usually we can ask to WordPress plugin team to adopt a plugin if the author does not answer to any message. And badly for this one they don’t want to let someone adopt it, you can read the answer from the WP.org team on the github repo.
W3TC and the Vulnerability
The vulnerability has been reported by Zerial. Let me explain it quickly:
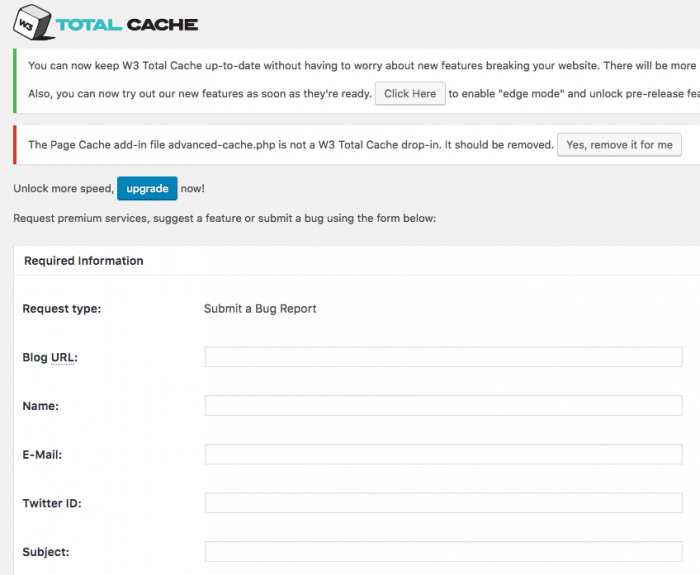
This page contains a support form, this page can be reach directly using a URL with params, then the params will fill the form.
Guess what, the params are not escaped when printed on the page, leading to an XSS vulnerability, simple as this.
Example of XSS URL to be avoided: https://example.com/wp-admin/admin.php?page=w3tc_support&request_type=bug_report&request_id=PAYLOAD
Then replace PAYLOAD with a malicious code.
D.R.E.A.D. SCORE
Here at WP Media we use the DREAD Scoring system to get the criticality of a vulnerability, let’s do this for this one, rated on 5 x 10 points:
Damage – How bad would an attack be?
Once done, you could add any JS/HTML injection code into the back-end of an admin WP area, then writing things, adding iframes, JS files, sending private data, security tokens, cookies.
Well i guess all of that at least.
10/10
Reproducibility – How easy is it to reproduce the attack?
A simple link with a raw JS/HTML code to be injected, no other skill required.
8/10
Exploitability – How much work is it to launch the attack?
Hide the link in a bit.ly like service, ask the admin to click. done.
Add an iframe with the forged link as HREF, ask admin to visit the page. done.
The “most difficult” part is finding the admin. But if you target a website, i guess you know who is it, you know the target, you know the admin.
8/10
Affected users – How many people will be impacted?
All and only admins.
4/10
Discoverability – How easy is it to discover the threat?
It’s full public now with no patch
10/10
Final DREAD Score
40/50
Ratings
Very Low (≤ 10)
Low (≤ 20)
Serious (≤ 30)
High (≤ 40)
Very High (≤ 50)
This XSS is rated HIGH RISK.
W3TC and Updates
I would like to say “Stay updated!” but I can’t. Samuel Woods told me that the author promises to update the plugin soon, “in a reasonable time frame” which is subjective. Waiting for this update, all people using W3TC today can be the target of this XSS attack.
How to avoid to be a target? The simplest way is to always disconnect your admin account, just use an author or editor one.
You can also choose another solution to improve the speed of your website.
We recommend you a plugin updated often, with a good and quick support. Free or premium, just remember that trying to avoid spending $40 for a plugin that will cost you more because of the vulnerabilities, the lack of support or updates is not a so good idea finally.
We, at WP Media, created WP Rocket, used by 120,000 websites, supported by a dedicated team. I’ll let you search for reviews and comparisons, I don’t want to tell you “we’re the best”, I’ll let that for our awesome users.
W3TC in the Future
What to think about this vulnerability, what to think about the next one, because you may now that when a vulnerability is discovered in a product, security consultant will try to find more, and there will be blood.
No update on W3 Total Cache SSRF reported over 4 months ago. Fix is basically adding 1 character #responsibledisclosure #wordpress #plugin
— Jouko Pynnönen (@klikkioy) September 23, 2016
Edit 09/26/2016: The plugin has been updated to 0.9.5, fixing this vulnerability.
Do you still want to use this plugin? Tell us why in the comments.


